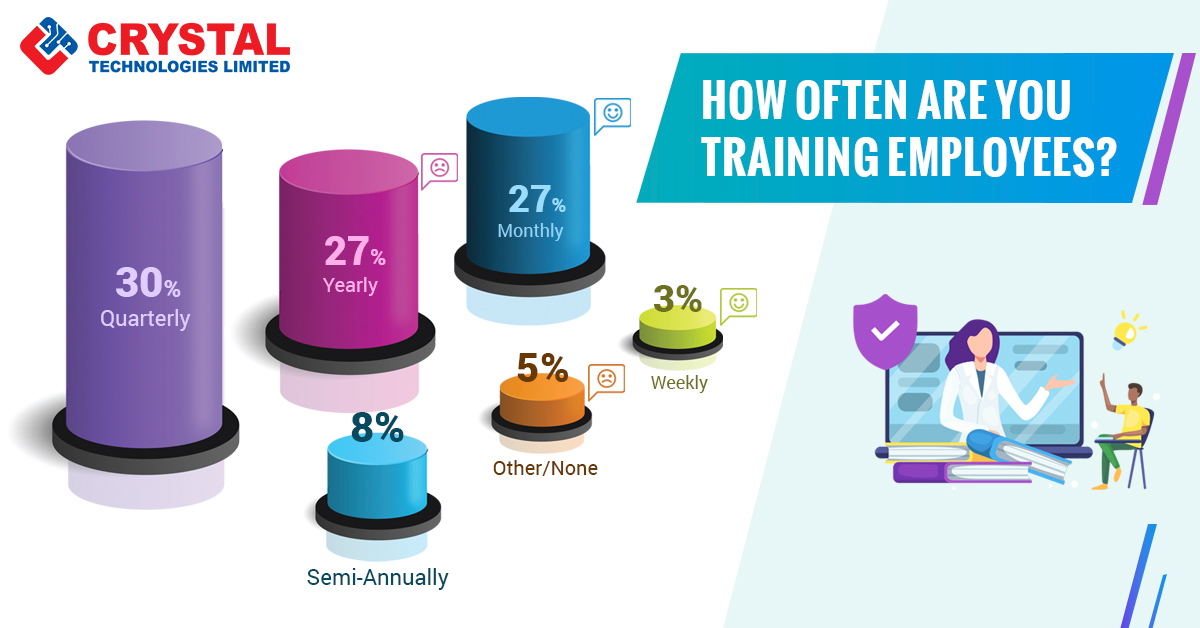
Your Biggest Cybersecurity Risk: Your Employees
Cybercriminals work round the clock to detect and exploit vulnerabilities in your business’ network for nefarious gains. The only way to counter these hackers is by deploying a robust cybersecurity posture that’s built using comprehensive security solutions. However, while you’re caught up doing this, there is a possibility you may…